Rainbow Six Siege Under Attack: How Hackers Broke in and Flooded Accounts with Billions of Credits
In late December 2025, Ubisoft’s flagship tactical shooter Rainbow Six Siege experienced a major security breach that allowed unknown attackers to gain unauthorised access to internal game systems and manipulate key backend functions. The incident became apparent when players worldwide noticed unusual activity on their accounts, including massive deposits of in-game currency and unexpected administrative actions, a sign that something beyond a routine outage was occurring.


Reports from players, and screenshots shared on social media, revealed that attackers had succeeded in abusing internal systems to grant approximately 2 billion R6 Credits and Renown to player accounts globally. R6 Credits are a premium in-game currency purchased with real money, used to unlock operators and cosmetics. Based on Ubisoft’s pricing, the unauthorised credits given out would be worth roughly $13.3 million if purchased legitimately.
In addition to the inflated currency, hackers unlocked every cosmetic item in the game, including developer-only skins and rare items, and were able to manipulate in-game moderation features, such as issuing bans and unbans across accounts, and displaying fake ban messages on the live moderation ticker.
Ubisoft was quick to acknowledge the incident on its official Rainbow Six Siege X (formerly Twitter) account, confirming teams were investigating. To contain the damage, the company shut down Rainbow Six Siege servers and the in-game Marketplace, halting live gameplay and transactions while engineers worked on a resolution.
Beyond the confirmed game service abuse, unverified claims emerged online suggesting the breach may have stemmed from a deeper compromise of Ubisoft’s infrastructure. A security research group reported that multiple threat actors claimed to have exploited a recent MongoDB vulnerability known as MongoBleed (CVE-2025-14847). This flaw, affecting certain MongoDB instances, allows unauthenticated attackers to leak memory contents, potentially exposing credentials, session tokens, or authentication keys. Some groups alleged they used this weakness to access Ubisoft’s internal services, ranging from a live game service to internal Git repositories, source code archives, and even user data.
At the time of reporting, Ubisoft had not released a detailed technical breakdown of the breach vector or confirmed whether the MongoBleed exploit was involved. While the immediate issue of currency manipulation was acknowledged and addressed through rollbacks and server downtime, the full extent of the incident, including whether sensitive internal assets or customer data were accessed, remained unclear. Ubisoft continued working toward a full restoration of services and investigating the incident further.
Trust Wallet Browser Extension Breach: $7 Million Lost in Major Crypto Supply-Chain Compromise
In late December 2025, a serious security incident, affecting the Trust Wallet Chrome browser extension, led to the theft of approximately $7 million worth of cryptocurrency from users’ wallets, a situation the company confirmed after users reported unauthorised draining of funds from their accounts starting around Christmas Eve.
The core of the problem was a compromised update to version 2.68 of the browser extension, which was published on the Chrome Web Store on 24 December 2025. Soon after that update became available and users interacted with it, attackers exploited malicious code embedded in the extension to exfiltrate sensitive wallet data, including recovery seed phrases, and then proceeded to drain funds from the affected wallets without user consent.
Trust Wallet, a widely used non-custodial cryptocurrency wallet that allows users to self-manage digital assets across multiple blockchains, quickly acknowledged the incident and urged users to immediately disable version 2.68 and upgrade to the patched version 2.69. The incident did not affect the mobile app or other extension versions, and the company stated it was investigating how the malicious update was able to be submitted and published.
The response from the broader crypto community and Trust Wallet’s owners was swift: Binance founder Changpeng “CZ” Zhao took to social media to confirm the losses and reassure users that Trust Wallet would cover the stolen funds so victims would be made whole despite the attack. Alongside this confirmation, BleepingComputer observed that threat actors also launched phishing domains that mimicked Trust Wallet support and offered fake “fixes” tricking some users into providing sensitive credentials that could be further abused.
The malicious code in the compromised extension allegedly communicated with an external server on a suspicious domain that was registered just days before the update, hinting at pre-meditated preparation by the attackers. Security analysts who examined the incident noted that the injected JavaScript code, masquerading as benign analytics logic, was designed to silently capture wallet information and send it outside the extension’s normal operation flow.
Trust Wallet and independent observers began quantifying the scope of the impact: thousands of wallets, estimated at around 2,596 addresses, saw funds drained, with losses impacting a variety of cryptocurrency networks including Bitcoin, Ethereum, and Solana, as attackers initiated automatic transfers shortly after wallets were accessed with the compromised extension.
While the company continues to work on investigations and reimbursements, this incident underscores the risks inherent in software supply chain attacks, especially for browser-based crypto tools where a compromised update mechanism can allow attackers to inject malicious code that users unknowingly install through official channels.
Marquis Software Data Breach: A Supply Chain Shock to US Community Banks and Credit Unions
In December 2025, Marquis Software Solutions, a Texas-based technology vendor providing data analytics, CRM, compliance reporting, and marketing services to over 700 community banks, credit unions, and mortgage lenders across the United States, disclosed a serious cybersecurity incident that has broad implications for the financial sector.
The breach originated from a ransomware attack that took place on 14 August 2025, when threat actors gained initial access through a SonicWall firewall used for remote access, a vector that has been exploited in similar attacks on other organisations. The attackers exfiltrated sensitive files before any encryption occurred, affecting systems that store customer data for dozens of financial institutions at once.
Because Marquis acts as a shared service provider, the impact extends far beyond a single bank, effectively turning one compromise into a cascading, multi-institution incident. Public breach notices filed with various US state attorneys general show that at least 74 banks and credit unions have been affected so far, involving data tied to hundreds of thousands of individuals.
The types of information that may have been copied by the attackers include, depending on the institution and account:
- Full names
- Mailing addresses and phone numbers
- Dates of birth
- Social Security numbers or Taxpayer Identification Numbers
- Bank account numbers
- Debit or credit card numbers
- Other financial account details (sometimes without security codes or PINs).
This mix of data provides enough information for identity theft, targeted fraud, phishing campaigns, and other financial crimes. Even if certain card security information was not present, the exposed personal identifiers are extremely valuable to threat actors. As of the latest public filings, there is no confirmed evidence that the stolen data has been posted online or misused, but regulators and affected banks have begun notifying customers and are offering support services such as credit monitoring.
Marquis has engaged external cybersecurity experts and reported the incident to federal law enforcement. In addition, it has worked with individual institutions to send notifications to affected customers and is reviewing its security controls.
This breach highlights a key risk in modern financial services: vendor and supply chain security vulnerabilities. When a single third party provider holds large volumes of sensitive customer data on behalf of many clients, a single breach can instantly affect multiple organisations. This “concentration risk” makes it harder for individual banks and credit unions to manage their own risk exposure and emphasises the need for robust third party risk assessments, visibility into vendor security practices, and strong perimeter defences.
https://socradar.io/blog/the-marquis-software-data-breach/
North Korean Hacker Machine Compromised by Infostealer Sheds Light on Bybit Crypto Heist Infrastructure
In December 2025, cybersecurity researchers uncovered an unusual and highly informative incident involving a North Korea-linked threat actor’s computer that had been infected with the LummaC2 infostealer, a type of malware typically used to steal credentials, cookies, and sensitive data from compromised systems. What makes this case especially notable is that the compromised machine appears to be part of the infrastructure supporting the $1.4 billion cryptocurrency heist against the Bybit exchange earlier in the year, providing rare visibility into the internal tools and operations of a state-linked cyber group.
The infection was detected by a cybercrime intelligence firm which was analysing a LummaC2 log when analysts realised the infected host belonged to someone involved in malware development within a North Korean state-linked cyber apparatus. When cross-referenced with data from another threat intelligence provider, Silent Push, the device was tied to accounts and domains used in the Bybit breach, long attributed to North Korean actors such as the Lazarus Group. One telling detail was an email address found on the infected machine that had been used to register a fake domain impersonating Bybit just prior to the heist, underscoring operational links between this system and the broader attack infrastructure.
Forensics on the compromised device revealed it was far from a casual setup. It was a well-equipped development machine with a 12th Gen Intel i7 CPU, 16 GB of RAM, and tools like Visual Studio Professional 2019 and Enigma Protector - the latter often used to wrap malware binaries to evade antivirus detection. Browser history and system configuration pointed to Astrill VPN usage with Simplified Chinese browser settings, alongside domestic language queries, suggesting efforts to obscure the operator’s origin. Analysis also found communication and file-sharing applications such as Slack, Telegram, Dropbox, and BeeBEEP - the latter often used for peer-to-peer messaging, indicating how threat actors coordinate and move stolen data.
The compromised system further showed preparations for phishing campaigns, with attackers having purchased domains designed to mimic legitimate services and entice victims into downloading fake software - including dummy Zoom installers hosted on subdomains like zoom.callapp.us. What makes this incident unusual is that the infostealer never realised it had infected an attacker’s machine; typically, LummaC2 is deployed against everyday targets to harvest credentials and browser session data. Instead, this infection inadvertently exposed part of the offensive tooling and infrastructure used by a sophisticated, state-linked cyber operation.
This accidental exposure offered cybersecurity researchers a rare window into the internal workings and practices of a threat actor linked to one of the largest crypto thefts in history. The firm even built a simulator replicating the compromised environment, enabling deeper inspection of software, data remnants, and stolen credentials recovered from the machine. While such operational mistakes are uncommon among nation state actors, they offer invaluable insight into tactics, techniques, and procedures, providing information that can help defenders and investigators better understand and counter similar threats in the future.
https://hackread.com/north-korean-hacker-device-lummac2-infostealer-bybit/
MuddyWater’s UDPGangster Backdoor: Iran‑Linked APT Deploys Stealthy UDP‑Based Malware in Regional Espionage Campaign
In December 2025, cybersecurity researchers revealed that the Iran‑aligned advanced persistent threat (APT) group MuddyWater has deployed a new backdoor malware named UDPGangster in targeted cyber‑espionage operations directed at organisations and users in Turkey, Israel, and Azerbaijan.
UDPGangster is a UDP‑based backdoor that leverages the User Datagram Protocol (UDP). By using UDP for communication with its C2 infrastructure, the malware can evade traditional network monitoring and detection systems that are often tuned for TCP‑based traffic, making it harder for defenders to spot and disrupt the malicious activity.
The threat actors behind this campaign used spear phishing emails to deliver the initial malware payload. These emails contained malicious Microsoft Word documents which, when opened and macros enabled, triggered execution of embedded malicious code that ultimately installed the UDPGangster backdoor on the victim’s system. Some of the phishing lures impersonated official organisations, such as the Turkish Republic of Northern Cyprus Ministry of Foreign Affairs, to increase the likelihood that recipients would trust the message and activate macro content, a common technique in targeted attacks.
Once launched, UDPGangster installs itself silently and achieves persistence on infected Windows hosts, typically copying itself into user directories and modifying system settings to ensure it runs after reboot. After establishing a foothold, the backdoor opens a UDP channel to its C2 server on port 1269, through which it can receive commands, execute arbitrary instructions, exfiltrate data, and deploy additional payloads at the attackers’ direction. Such techniques reflect a growing trend among sophisticated APT actors to invest in stealthy malware that can maintain long‑term access without raising alerts.
MuddyWater - also tracked under names such as APT39, Static Kitten, and Mercury - has a history of deploying custom malware and spear phishing campaigns targeting government, telecommunications, energy, and other strategically significant sectors, particularly in the Middle East and surrounding regions. The group is widely assessed to have ties to Iranian state interests and conducts espionage operations aligned with geopolitical objectives.
The deployment of UDPGangster demonstrates how state‑linked actors continue to innovate with non‑standard C2 protocols and social engineering techniques, increasing the challenge for defenders tasked with protecting high‑value targets. Organisations in geopolitically sensitive regions - especially those handling government, infrastructure, or critical data - should remain vigilant against macro‑based phishing and implement network monitoring capable of flagging unusual UDP communications and unauthorised outbound connections.
https://thehackernews.com/2025/12/muddywater-deploys-udpgangster-backdoor.html
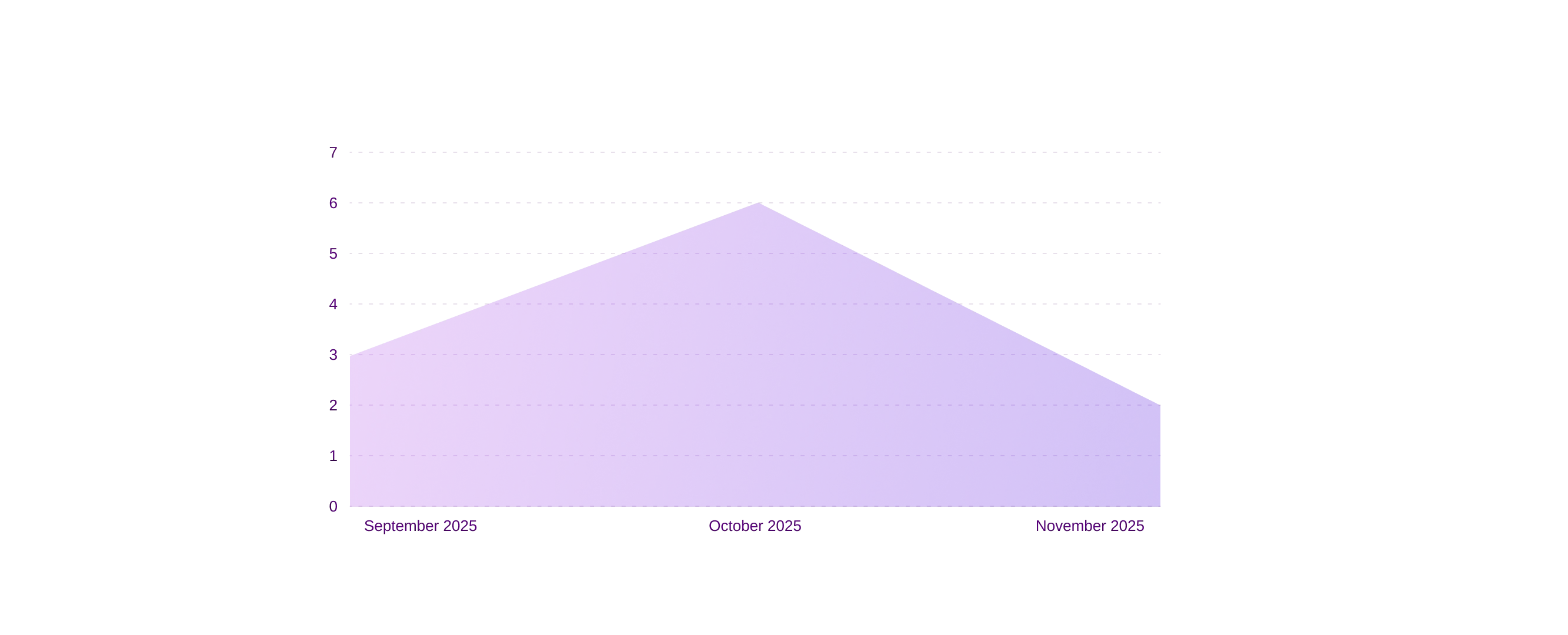
Threat actors targeting financial entities in December 2025

Ransomware vs Finance (last three months)

Managing Risk of AI Adoption
AI is transforming how organisations across the globe work, from powering internal knowledge hubs and embedding tools like CoPilot in Teams, to generating production-ready code. But every innovation brings new cyber risks, compliance challenges, and attack surfaces. By utilising our AI code testing service, you can ensure your AI deployments are resilient, compliant, and ready for the real world.
Insights

State‑Aligned Threat Actors Target Critical Infrastructure and Individuals
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

Advanced Malware and Supply Chain Shocks
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

2025 Cyber Round-Up: The Threat Evolution
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

Data Breaches Surge Across All Sectors, Exposing Sensitive Data and Reducing Digital Trust
Stay ahead of the curve with this month’s Cyber Risk Newsletter, your essential briefing on the evolving threat landscape.

